Fraud attacks on banks are becoming more common and attackers use sophisticated methods to steal big amounts of money. We have witnessed several large attacks on ATMs globally over the past few months; in Thailand, India, Latin America, across Europe, …
Out of all the cybercrimes from malware to social engineering, the creepiest has to be a stranger watching your child through a webcam or baby monitor in their room. As this year’s Mobile World Congress starts in Barcelona, Avast researchers reveal that half a million smart devices in the city, including webcams and baby monitors, are currently vulnerable to cyber attack.
Locky ransomware, a variant of ransomware that scrambles your files, changes all the names, and then demands payment to unscramble them and release them back to you, has taken a holiday of sorts. Avast detection of Locky shows that attacks have slowed …
Do you have more than one Twitter or WhatsApp account? If you answered yes, do you want to log in to these multiple accounts at the same time? Up until this point, logging in to multiple social media accounts at one time has only been possible by usi…
Linux flaw affects about 1.4 billion Android devices
The newly discovered Linux flaw allows hackers to carry out attacks on Android users using a Man-in-the-Middle (MITM) Transport Layer Security (TLS) Protocol Downgrade Attack. In layman’s term…
This week we released a new version of our core PC antivirus product, which we refer to as the Avast Antivirus Nitro Update. The update’s name is Nitro, because it is filled with innovative, new ways to increase speed and increase protection. One of the new ways we are increasing protection is with a cool new proprietary technology called CyberCapture. CyberCapture dramatically raises the bar when it comes to protection against zero-second attacks.
 CyberCapture looks at the smallest bits of a file to determine its safety
CyberCapture looks at the smallest bits of a file to determine its safety
Let me explain how it works, and take a look at the infographic below which shows the path of an unknown file.
Guess who hackers disguised themselves as in a recent phishing campaign? That’s right – Avast! A laughable fake Avast alert email is trying to harvest webmail addresses, being sent out via a spam message and leading to several domains where attackers have prepared a simple form to collect victims’ email addresses and passwords.
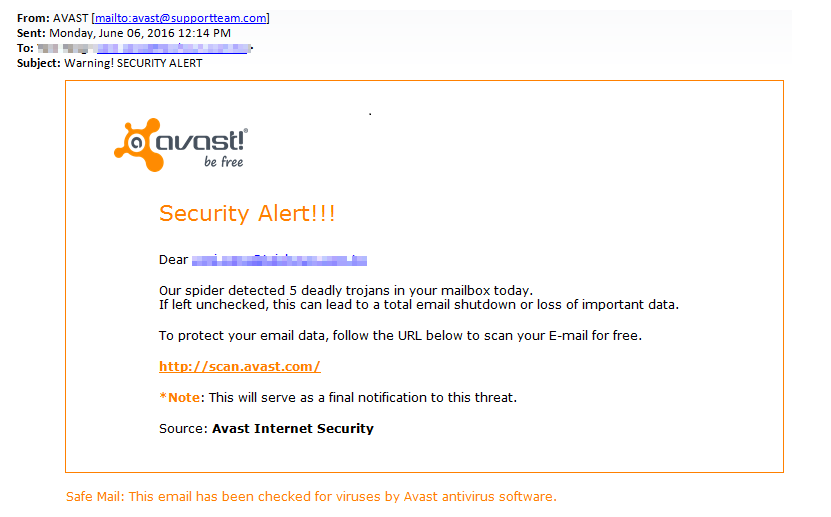
Received spam in a phishing scheme impersonating Avast
Fake football apps appear on the Google Play Store in time for Copa America and Euro Cup.
Copa America Centenario and Euro Cup start this Friday and next Friday respectively, and everyone across the Americas and Europe are in the football/soccer …
Copa America Centenario and Euro Cup are starting this Friday and next Friday, respectively, and everyone across the Americas and Europe are in the football/soccer spirit.
I found four soccer/football apps on the Google Play Store, all with the same or similar names, that are pretty bad knock-offs of the popular FIFA app. All four apps have negative reviews claiming the apps do practically nothing but display ads. Clearly, the person or people behind these apps only intention is to make money and not to deliver quality apps.
I dug a little deeper and despite the fact that these four apps were uploaded under different developer names, they seem to be developed by one developer. All four apps have the same dex files and manifests. Each developer name has only uploaded one app and there are no links to any developer homepages.
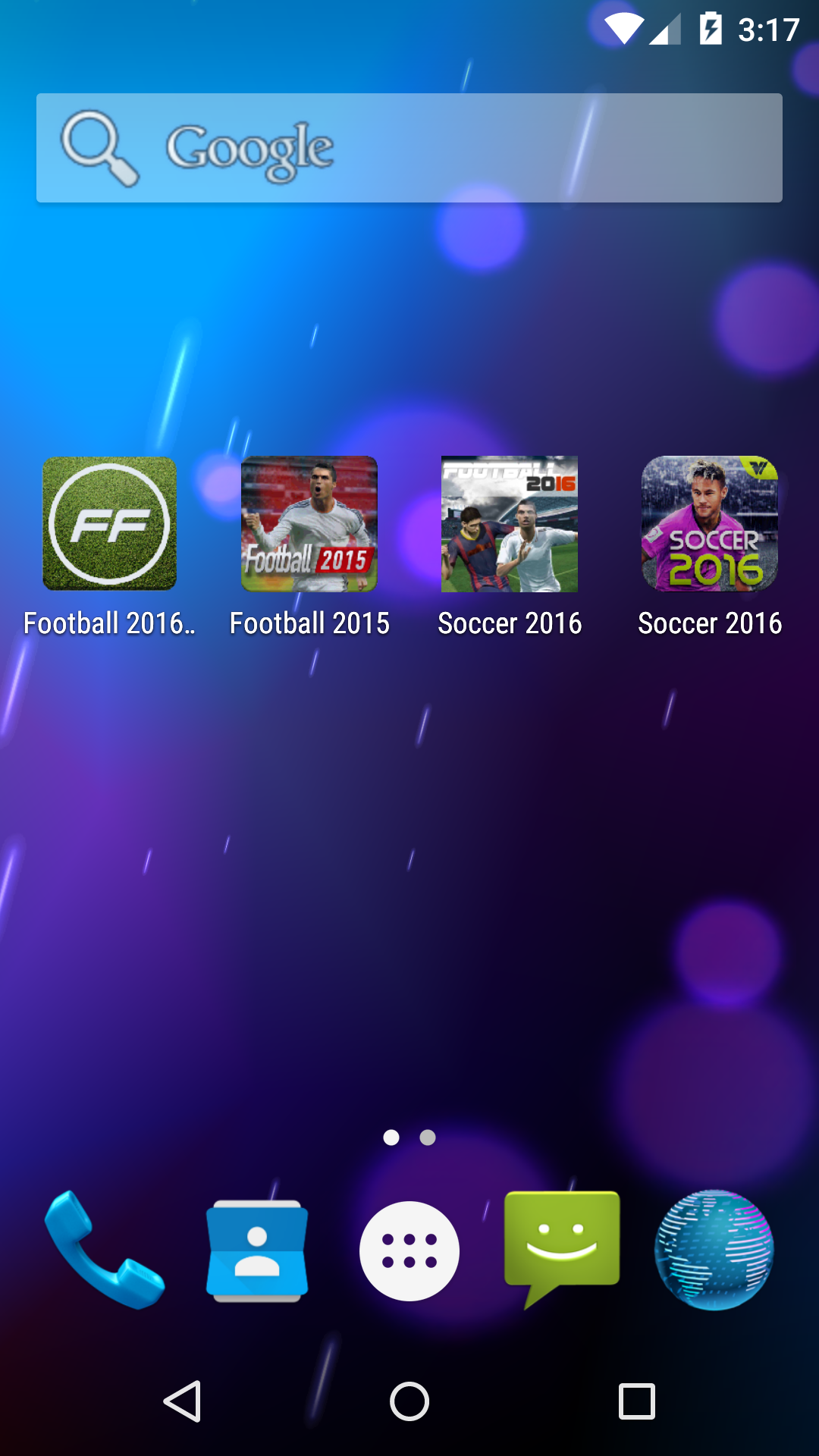
I decided to test each app to see if the negative reviews regarding the ads were true and unfortunately, they are…
An Android Trojan is spying on its victims and even tricking some into giving up their credit card information.
Most of today’s malware authors create malware for one of two reasons: either to make money or to steal valuable data. In this blog post, we will show how an Android Trojan relies on social engineering. Social engineering tactics are used to trick people into performing an action, like clicking on a link or downloading an application. The person being tricked thinks they are doing something innocent when they are really clicking on or downloading something malicious. This malware is associated with the banker family as it tries to steal user’s credit card information.
Once installed, the Banker Trojan puts an icon in the launcher.The app name shown with the icon can vary from sample to sample — some of the names we have seen were : AVITO-MMS, KupiVip and MMS Центр (MMS Center).
 CyberCapture looks at the smallest bits of a file to determine its safety
CyberCapture looks at the smallest bits of a file to determine its safety
