LinkedIn members’ login credentials are being sold on the dark web.
The 2012 breach of social networking site LinkedIn, has come back to haunt us. That breach resulted in 6.5 million members’ credentials being stolen. Articles published in t…
A brief update on Locky, the latest ransomware targeting PCs.
Beware of emails from random email addresses with subject lines like “Upcoming Payment – 1 Month Notice”. These emails typically come with a zip attachment that attackers have created to run a script that downloads and runs the now well-known ransomware, Locky. These phishing emails prove that Locky is not going anywhere anytime soon.
Last week, Talos discovered multiple vulnerabilities in 7-Zip, a popular, open source file archiver. The vulnerabilities are particularly severe as many products, including antivirus software, implement 7-Zip in their software. When vulnerabilities are found, it is the responsibility of software owners to patch them. However, these patches are useless, unless users update their software.
Avast is not affected by these vulnerabilities, but if you are a non-Avast user we recommend you update your antivirus software, if you haven’t done so already.
Avast Passwords gives you easy, secure access to all your passwords, PINs and login credentials.
Avast Passwords is an app that helps you to safely store each of your PIN codes, passwords and login details safely in one place. Instead …
Most of popular botnet Andromeda’s (also known as Gamarue) distribution channels have been discovered and analyzed by antivirus vendors. This has forced Andromeda’s distributors to come up with a new attack strategy to continue to drop Andromeda binaries onto PCs.
Meanwhile at the Andromeda headquarters…
Operator: “Captain, all of our distribution channels have been discovered!”
An Android Trojan is spying on its victims and even tricking some into giving up their credit card information.
Most of today’s malware authors create malware for one of two reasons: either to make money or to steal valuable data. In this blog post, we will show how an Android Trojan relies on social engineering. Social engineering tactics are used to trick people into performing an action, like clicking on a link or downloading an application. The person being tricked thinks they are doing something innocent when they are really clicking on or downloading something malicious. This malware is associated with the banker family as it tries to steal user’s credit card information.
Once installed, the Banker Trojan puts an icon in the launcher.The app name shown with the icon can vary from sample to sample — some of the names we have seen were : AVITO-MMS, KupiVip and MMS Центр (MMS Center).
From football stars to cheating spouses, using easy-to-crack passwords puts everything from your livelihood to your relationships at risk.
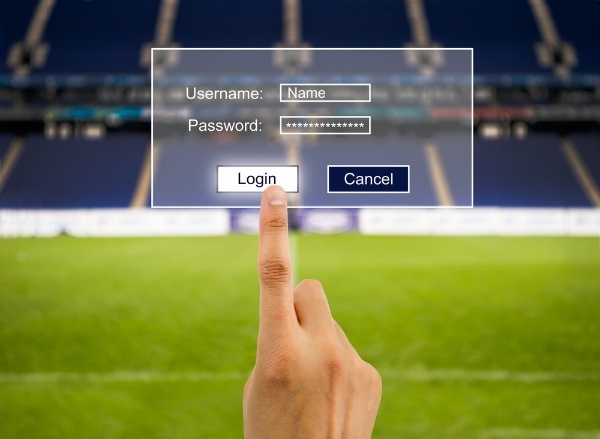 Change your passwords regularly and don’t share them with others
Change your passwords regularly and don’t share them with others
A tweet showing top NFL draft pick Laremy Tunsil taking a hit off a bong through a gas mask cost him upwards of $13 million. Tunsil’s Twitter account was allegedly hacked at the worst time – just minutes before the draft began – making his fall from the first round to thirteenth swift, decisive, and oh, so costly. Minutes after that, his Instagram account was hacked to show screenshots of a text conversation implicating Ole Miss in NCAA rule-breaking that will likely end up in an investigation.
This mind-boggling turn of events in what should have been a night of triumph for Tunsil and his university has a lesson for the rest of us.

News broke that Australian businessman Craig Steven Wright is Satoshi Nakamoto earlier this week.
(Image via the Wall Street Journal)
Finally, we know the inventor of bitcoin! Wait, maybe not so fast. Actually, we don’t know anything at all.
A new phishing campaign takes advantage of Facebook’s security measures in order to appear legitimate. In this case, the creators of the campaign have created an app which is, in essence, a simple <iframe> that displays a fraudulent version of Facebook’s login page. Cybercriminals are abusing the Facebook application platform to carry out phishing campaigns against users which appear legitimate thanks to the fraudulent use of Facebook’s own Transport Layer Security (TLS) security certificates, a protocol used to help keep domains and user communication secure.
The phishing web site is hosted on hxxp://gator4207.hostgator.com/~labijuve/a2/, which leads to a identical yet fake copy of Facebook’s verification page.Despite the resemblance that the iframe bears to Facebook’s actual webpage, the differences between the two sites become obvious when they’re displayed next to one another.

