Mr. Robot Review: eps2.9_pyth0n-pt2.p7z
This season finale had me sitting in front of the TV saying “what?” a couple of times – a sign that this was another great episode!
This season finale had me sitting in front of the TV saying “what?” a couple of times – a sign that this was another great episode!

Digitization – the use of social, mobile, analytics, and cloud technologies to generate, process, store and communicate data – is transforming everything, with profound implications on how we learn, work and play.
“Digital transformation is not just a technology trend, it is at the center of business strategies across all industry segments and markets,” stated IDC.
Petya and Mischa ransomware, come as a package deal, distributed by its creators, Janus. They are very unusual in that they combine two different methods to encrypt user data. Unlike most other ransomware, Petya primarily encrypts MFT (Master File Tabl…
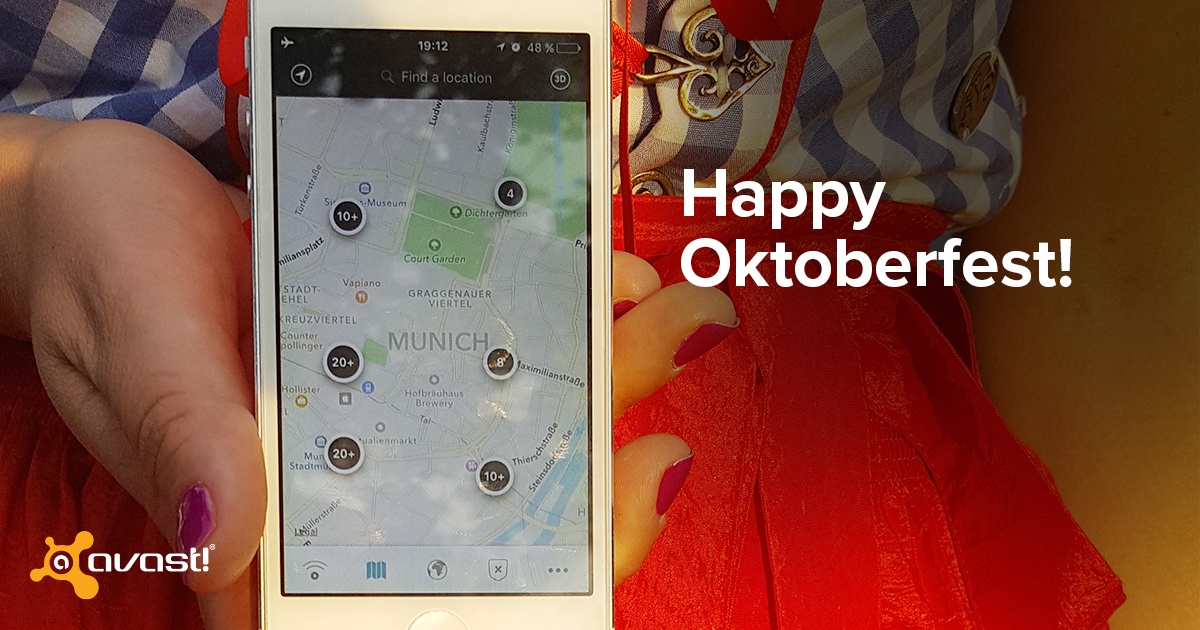
This Saturday, the 183rd Oktoberfest will take place on the Theresienwiese in Munich, Germany. People will travel to the Bavarian capital from all over the world to enjoy beer, music, chicken, cotton candy, amusement rides and more!
If you are traveling to Munich for Oktoberfest, you probably want to share your exciting beer hall photos and videos with friends and family to show off (as soon as possible) what an awesome time you are having! You may also need to access Google Maps to find your way around the city while sightseeing. Now, you’re probably asking yourself: How am I going to do this, unless I pay for an expensive international plan?
Things are slowly starting to come together, as they should be considering this was the second to last episode of the season!

Zepto ransomware is a relatively new player in the ransomware scene, and it’s closely related to the infamous Locky ransomware. Taking a closer look at Zepto’s code, we found that the code is pretty much the same as Locky’s code, but it has been slightly modified. The malware authors behind Zepto use the same methods used to spread Locky, and even the infection vector and the TOR payment page are the same, which makes us think that the people behind Locky are now spreading Zepto. The only difference between Locky and Zepto is the ransom demand. Zepto’s demand is much higher than Locky’s, 3 Bicoins (approximately $1,850).
I honestly do not know where to begin with this week’s episode of Mr. Robot, I am still in a bit of shock! Elliot only carried out one hack, but many other things unraveled, leaving with me with so many questions.
Image via: USA Network @whoismrrobot
Dropbox has suffered a password dump of epic proportions. (Image via Graham Cluley)
Dropbox has been going through some rough times as of late. In the past 24 hours, headlines have been popping up left and right about a Dropbox password dump of epic…